The API Security Problem
(Note: If you'd like more on the OWASP API Top 10 then take a look at my Pluralsight course on OWASP Top 10: API Security Playbook)
There are many things on the internet that don’t get the security thought they need. The problem with API security is that in recent years the number of APIs that exist has hugely increased, while the thought to API security hasn’t gone very far at all.
What do we mean by an API? While people need a nice user interface like a website to use web services, often in the form of HTML, computers need no such thing. For them, the interface is purely about data, which is exactly what an API (Application Programming Interface) provides. You communicate with an API with data, not buttons, forms or drop down boxes.
Why do APIs not get much security love? They’re often seemingly invisible, unlike a web site which has an obvious way to interact with it. If you can’t see it then it’s not a problem, great! No.
What does a HUGE increase look like?

Why has there been a huge increase in the number of APIs? That’s a big one…
Websites
Web servers historically created a web page populated with data and sent it back to the browser. Data and HTML would be merged on the server before going to the client. It’s now becoming more common to see a clear separation between the user interface and the data in use. That means a web page is displaying data that it retrieves from an API. That merging of HTML and data happens at the client instead of the server.
Internet of Things (IoT)
The Internet of Things is massive and growing rapidly. When we say IoT, what we mean is the billions of devices that are connected to the internet all by themselves. This means internet connected lightbulbs, kettles, refrigerators etc. How do they communicate over the internet? APIs.
In 2020 there were an estimated 5.8 billion IoT devices. The 2025 estimate is over 41 billion.
Mobile Applications
With smartphones come applications. How many of them do you think call out onto the internet (using APIs) to help them work (or pass on your personal data)?
2020 figures suggest 1.85 million iOS apps and 2.56 million Android apps. That makes for a lot of APIs and its only going to grow.
Machine to Machine
Often APIs use functionality from other APIs, so when a request is made to an API, that may then trigger requests to other APIs. This happens because functionality takes a lot of effort to get right and sometimes it’s easier to use that functionality in someone else’s API than it is to create it yourself. From taking card payments to postal code lookups, one API can utilise lots of others.
So there are millions of APIs on the internet and that number is likely to increase. The security around APIs is often lacking. The more APIs there are, the more attention they attract from criminals, intent on stealing data and abusing their resources.
Worryingly, APIs are becoming the norm in areas such as healthcare and financial services:
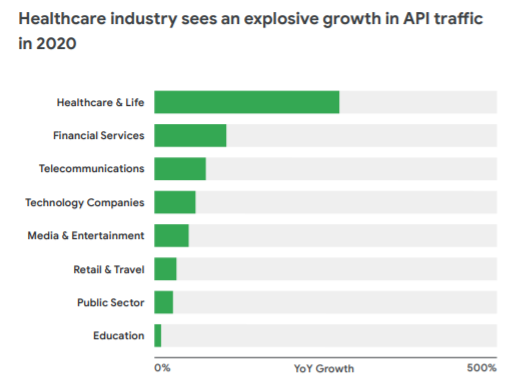
This is understandable. In terms of providing web based services, APIs are often a very good proposition and make a lot of sense from an architectural point of view. As long as they’re being developed securely then they’re often a good choice.
What security issues do APIs face? The Open Web Application Security Project (OWASP) has a top ten of security issues to look out for in APIs. The issues reflect those generally found on websites as there is a lot of commonality in the way they work and communicate across the internet . Of course there are more than just 10 issues that can affect an API, but this list is a great start! With awareness of a list like this, security can really improve, but how much awareness is there?
The OWASP API Security top 10 was released in 2019, so it’s clear that this wasn’t a great concern before then. In the developer community, awareness of the API top 10 is generally quite low, with importance being placed on the original OWASP top 10, which focused on websites and not APIs. Awareness of that top 10 is a great start, but it’s easy to miss the importance of security in APIs.
What does the OWASP security top 10 look like?
- Object Level Authorization – does the API correctly apply permissions stopping one user from seeing data belonging to another user?
- Broken User Authentication – is the authentication process free from common failures that might allow a malicious user to login as another user
- Excessive Data Exposure – does the API leak information that should be private?
- Lack of Resources & Rate Limiting – does the API fail to restrict the number of requests that can be made, allowing bad things to happen, like databases being overwhelmed with requests?
- Broken Function Level Authorization – can a regular user also call functionality that should be reserved for administrators or users with different sets of permissions?
- Mass Assignment – if you make a request, can you include additional fields to alter the result of the request?
- Security Misconfiguration – there are so many ways in which you can misconfigure your security it’s almost unbelievable.
- Injection – can you include a value in a request that alters the intended use, for example, can you make a database request that retrieves data from a different database table than the one that was intended?
- Improper Assets Management – are non-production environments vulnerable because they lack the necessary security controls? Maybe they need less controls than the production environment, but that needs to be given consideration.
- Insufficient Logging & Monitoring – Can your logging identify security problems and help you to mitigate them?
Okay, that’s a very brief look at the OWASP API Security Top 10, but it’s becoming an incredibly important part of software development. If you’re not considering security when you’re writing an API then you’re taking a big risk with the data and resources it has access to!
Got a comment or correction (I’m not perfect) for this post? Please leave a comment below.
Subscribe to Gavin Johnson-Lynn
Get the latest posts delivered right to your inbox